Highest praise–I wish I had thought of this. I’d provide the original website where I saw it, but I don’t remember. It was so easy to replicate I didn’t record the URL.
Port forwarding is dangerous from a security standpoint. However, it is necessary to penetrate the firewall to accept connection requests that originate outside of the home network–i.e., act like a server. Typically, this is done safely with a firewall appliance. These are expensive and complicated.
Most geeky people have a second router floating around; router upgrades these days typically are based on improved WiFi function rather than wired enhancements. This was my situation, the happy owner of an old gigabit Ethernet device but with older WiFi, and a newer router with a newer WiFi implementation.
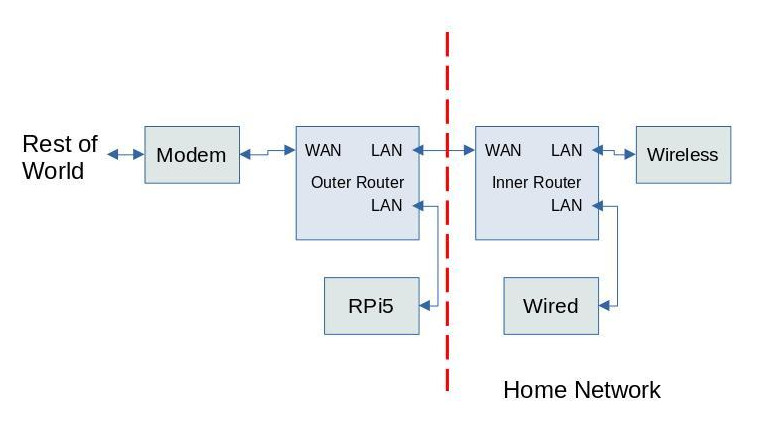
The WAN port on the older, OUTER router is attached to the modem. One LAN port serves the RPi5. Port forwarding is enabled on this router, and the DDNS update client is enabled on this router.
A second LAN port on the OUTER router connects via Ethernet to the WAN port of the INNER router. The wired and wireless connections originating from the LAN ports on my INNER router to my various computers, printers, and devices are set up normally. My wireless setup is a little funky, using an external mesh connected to a LAN port, but a typical wireless setup originating from the router would function normally.
Because the OUTER router is connected to the WAN port of the INNER router, as far as the INNER router is concerned, everything going on with respect to the OUTER router (i.e., the server) is occurring in the potentially hostile REST OF WORLD. The INNER router firewall has no port forwarding and all security settings are at their maximum.
I haven’t noticed any significant slowdowns, but I don’t play games. Netflix and other streaming services are perfectly happy.